Abstract
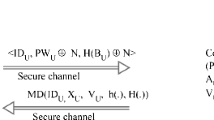
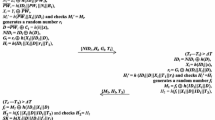
Remote user authentication is desirable for a Telecare Medicine Information System (TMIS) for the safety, security and integrity of transmitted data over the public channel. In 2013, Tan presented a biometric based remote user authentication scheme and claimed that his scheme is secure. Recently, Yan et al. demonstrated some drawbacks in Tan’s scheme and proposed an improved scheme to erase the drawbacks of Tan’s scheme. We analyze Yan et al.’s scheme and identify that their scheme is vulnerable to off-line password guessing attack, and does not protect anonymity. Moreover, in their scheme, login and password change phases are inefficient to identify the correctness of input where inefficiency in password change phase can cause denial of service attack. Further, we design an improved scheme for TMIS with the aim to eliminate the drawbacks of Yan et al.’s scheme.




Similar content being viewed by others
References
Leng, L., Teoh, A.B.J., Li, M., Khan, and M.K., A remote cancelable palmprint authentication protocol based on multi-directional two-dimensional palmphasor-fusion. Sec. Commun. Netw., 2013. doi:10.1002/sec.900
Khan, M.K., and Kumari, S., An authentication scheme for secure access to healthcare services. J. Med. Syst. 37(4):1–12, 2012
Kumari, S., Khan, M.K., and Kumar, R., Cryptanalysis and improvement of a privacy enhanced scheme for telecare medical information systems. J. Med. Syst. 37(4):1–11, 2012
Cao, T., and Zhai, J., Improved dynamic ID-based authentication scheme for telecare medical information systems. J. Med. Syst. 37(2):1–7, 2013
Chen, H.M., Lo, J.W., and Yeh, C.K., An efficient and secure dynamic ID-based authentication scheme for telecare medical information systems. J. Med. Syst. 36(6):3907–3915, 2012
Debiao, H., Jianhua, C., and Rui, Z., A more secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1989–1995, 2012
Lin, H.Y., On the security of a dynamic ID-based authentication scheme for telecare medical information systems. J. Med. Syst. 37(2):1–5, 2013
Wei, J., Hu, X., and Liu, W., An improved authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3597–3604, 2012
Wu, Z.Y., Lee, Y.C., Lai, F., Lee, H.C., and Chung, Y., A secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1529–1535, 2012
Xie, Q., Zhang, J., and Dong, N., Robust anonymous authentication scheme for telecare medical information systems. J. Med. Syst. 37(2):1–8, 2013
Zhu, Z., An efficient authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3833–3838, 2012
Leng, L., Zhang, J., Khan, M.K., Chen, X., Ji, M., and Alghathbar, K., Cancelable palmcode generated from randomized gabor filters for palmprint template protection. Sci. Res. Ess. 6(4):784–792. 2011
Leng, L., and Zhang, J., Palmhash code vs. palmphasor code. Neurocomput., 2012
Khan, M.K., Zhang, J., and Alghathbar, K., Challenge-response-based biometric image scrambling for secure personal identification. Futur. Gener. Comput. Syst. 27(4):411–418, 2011
Khan, M.K., Zhang, J., and Tian, L., Protecting biometric data for personal identification. In: Advances in Biometric Person Authentication: Springer, 629–638, 2005
Tan, Z., An efficient biometrics-based authentication scheme for telecare medicine information systems. Network 2(3):200–204, 2013
Yan, X., Li, W., Li, P., Wang, J., Hao, X., and Gong, P., A secure biometrics-based authentication scheme for telecare medicine information systems. J. Med. Syst. 37(5):1–6, 2013
Jin, A.T.B., Ling, D.N.C., and Goh, A., Biohashing: two factor authentication featuring fingerprint data and tokenised random number. Pattern Recog. 37(11):2245–2255, 2004
Belguechi, R., Rosenberger, C., and Ait-Aoudia, S., Biohashing for securing minutiae template. In: 20th International Conference on Pattern Recognition (ICPR), 1168–1171, 2010
Lumini, A., and Nanni, L., An improved biohashing for human authentication. Pattern Recogn. 40(3):1057–1065, 2007
Yang, C., Integration of Biometrics and Pin Pad on Smart Card. PhD thesis: University of Newcastle Upon Tyne, 2011
Brier, E., Clavier, C., and Olivier, F., Correlation power analysis with a leakage model. In: Cryptographic Hardware and Embedded Systems-CHES: Springer, 16–29, 2004
Eisenbarth, T., Kasper, T., Moradi, A., Paar, C., Salmasizadeh, M., and Shalmani, M.T.M., On the power of power analysis in the real world: A complete break of the keeloq code hopping scheme. In: Advances in Cryptology–CRYPTO: Springer, 203–220, 2008
Kocher, P., Jaffe, J., and Jun, B., Differential power analysis. In: Advances in CryptologyCRYPTO99: Springer, 388–397, 1999
Messerges, T.S., Dabbish, E.A., and Sloan, R.H., Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 51(5):541–552, 2002
Boyd, C., and Mathuria, A., Protocols for Authentication and Key Establishment: Springer, 2003
Yang, C.C., Yang, H.W., and Wang, R.C., Cryptanalysis of security enhancement for the timestamp-based password authentication scheme using smart cards. IEEE Trans. Consum. Electron. 50(2):578–579, 2004
Juang, W.S., Lei, C.L., and Chang, C.Y., Anonymous channel and authentication in wireless communications. Comput. Commun. 22(15):1502–1511, 1999
Khan, M.K., Kim, S.K., and Alghathbar, K., Cryptanalysis and security enhancement of a ‘more efficient & secure dynamic ID-based remote user authentication scheme. Comput. Commun. 34(3):305–309, 2011
Xu, J., Zhu, W.T., and Feng, D.G., An efficient mutual authentication and key agreement protocol preserving user anonymity in mobile networks. Comput. Commun. 34(3):319–325, 2011
Li, C.T., and Hwang, M.S., An efficient biometrics-based remote user authentication scheme using smart cards. J. Netw. Comput. Appl. 33(1):1–5, 2010
Li, X., Niu, J.W., Ma, J., Wang, W.D., and Liu, C.L., Cryptanalysis and improvement of a biometrics-based remote user authentication scheme using smart cards. J. Netw. Comput. Appl. 34(1):73–79, 2011
Truong, T.T., Tran, M.T., and Duong, A.D., Robust biometrics-based remote user authentication scheme using smart cards. In: 15th International Conference on Network-Based Information Systems (NBiS), 384–391, 2012
Chang, Y.F., Yu, S.H., and Shiao, D.R., A uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. J. Med. Syst. 37(2):1–9, 2013
Lee, C.C., and Hsu, C.W., A secure biometric-based remote user authentication with key agreement scheme using extended chaotic maps. Nonlinear Dyn. 71(1–2):201–211, 2013
Potlapally, N.R., Ravi, S., Raghunathan, A., and Jha, N.K., A study of the energy consumption characteristics of cryptographic algorithms and security protocols. IEEE Trans. Mobile Comput. 5(2):128–143, 2006
Wong, D.S., Fuentes, H.H., and Chan, A.H., The performance measurement of cryptographic primitives on palm devices. In: 17th Annual Computer Security Applications Conference (ACSAC-2001), 92–101, 2001
Acknowledgments
The authors thank the anonymous referees for their valuable comments that helped to improve the presentation of the paper. Third author (Dr. Ankita Chaturvedi) is thankful to National Board for Higher Mathematics (NBHM), Mumbai, India, for their financial support. One co-author (Dr. Muhammad Khurram Khan) research was partially funded by National Natural Science Foundation of China (NSFC) under Grant no. 61300220 and 61371098.
Author information
Authors and Affiliations
Corresponding author
Additional information
Conflict of interests
The authors declare that they have no conflict of interest.
This article is part of the Topical Collection on Patient Facing Systems
Rights and permissions
About this article
Cite this article
Mishra, D., Mukhopadhyay, S., Chaturvedi, A. et al. Cryptanalysis and Improvement of Yan et al.’s Biometric-Based Authentication Scheme for Telecare Medicine Information Systems. J Med Syst 38, 24 (2014). https://doi.org/10.1007/s10916-014-0024-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-014-0024-2